Ultimate Guide to Botnet Attacks and Data Protection

Have you ever wondered how hackers simultaneously control thousands, even millions, of devices? That’s nothing but the power of a botnet—a term that might sound like a sci-fi villain but is an actual hazard to your cybersecurity.
Let’s break it down, apprehend how botnet attacks work, and, most importantly, how to shield yourself from becoming an unknowing pawn in their game.
So, without further ado, let’s get started!
Happy reading!
A botnet is a group of net devices (laptop systems, smartphones, and IoT gadgets) infected with malicious software programs and controlled by way of a hacker.
These compromised devices, or “bots,” collaborate to perform cyberattacks like:
Here’s the horrifying part: You might not even recognize that your devices are part of a botnet! That’s why data security and safety are crucial.
It might start with malware that hampers your devices. Let’s understand how hackers distribute this malware:
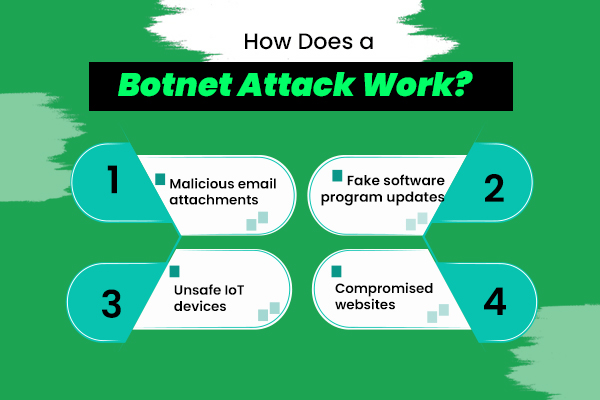
Once the malware infects your devices, it adds it to the hacker’s botnet, giving them remote control.
Scary, isn’t it?
Now, your device can get cyberattacks without your consent and knowledge.
Related Read: How Anti-Tracking Software Can Shield Your Data: Say Goodbye to Trackers!
A botnet attack calculatedly reveals that every device is designed to exploit vulnerabilities and gain access to multiple devices for malicious purposes.
Here’s a breakdown of the different stages of a botnet attack:
Hackers must first seek out device, network, or software vulnerabilities. Such vulnerabilities can entail outdated software packages, weak passwords, or poorly secured IoT devices. These factors are attractive points for a cyberattack.
When weaknesses are discovered, malware is launched to toxify consumer gadgets. An attack may occur indirectly via phishing emails, malicious downloads and links, or compromised websites. The device becomes part of the botnet without the consumer being aware once the malware has been installed.
After getting access to more than one gadget, hackers mobilize their botnets to exercise huge attacks. These can encompass Distributed Denial of Service (DDoS) attacks, information breaches, sending unsolicited emails, or mining cryptocurrency.
The synchronized energy of more than one gadget amplifies the impact of those moves.
Understanding the botnet attack stages helps users take different neutralized measures to keep the devices uninfected and secure.
Thwart botnet attacks and protect your devices with AVP Suite’s protection against botnet threats.
Claim Your Free Trial!
Well, what’s the best news? Although botnet attacks sound scary, honestly, they are; however, you can stay away from botnet attacks, too!
Let’s check the preventive steps to safeguard your devices:
A strong antivirus software program malware removal device like AVP Suite Antivirus Software can detect and neutralize malware long before it reaches your devices. AVP Suite offers real-time protection, blocking threats and protecting your devices.
An outdated device is a hackers’ paradise. Hackers utilize the vulnerabilities in outdated software. Regular updates can shield your devices from those security vulnerabilities, making it more difficult for malware to slide through your device. If feasible, enable automobile updates.
Weak passwords make it easy for hackers to take over devices. Use letters, numbers, and special character combinations, and avoid reusing passwords across different accounts.
Never click on hyperlinks or download attachments from unknown sources. These are not unusual access points for botnet malware and keep hackers at bay.
Your smart home devices, like cameras and thermostats, are top targets for botnets. Change default passwords, replace firmware often, and use a safe Wi-Fi network.
Firewalls act as a barrier between your devices and unauthorized access to your devices. Ensure your firewall is activated and configured efficiently.
Also Read: A Guide on Online Data Protection: 5 Times To Say No to Website Cookies
This is where AVP Suite antivirus software enters the scene! With multiple robust and cutting-edge features designed to protect against botnets and other threats, the AVP Suite offers:
With AVP Suite, you don’t have to worry about botnets compromising security and safety.
Read More: How to Access the Dark Web?: A Comprehensive Guide
The internet is not always safe; however, you don’t need to deal with it alone! We’re there for you! With AVP Suite Antivirus Software, you get impenetrable cybersecurity that keeps you ahead of threats. So, don’t wait until your device is part of a botnet—act now!
Ready to secure your digital world? Try AVP Suite today and enjoy peace of mind like never before. Protect your devices, protect your data, and browse with confidence!
Your security is worth it—don’t let botnets control you.